Spooling might sound complex, but it's an important concept in cyber security that everyone should know about. Essentially, spooling in cyber security is when data is temporarily held in an area of a computer's memory, allowing different programs to access it when they're ready.
In this segment of EssayService subjects, we'll break down what the concept really means, explore its benefits and drawbacks, and share some straightforward tips on how you can protect your system from potential risks associated with spooling.
What is Spooling?
Spooling manages how data moves between your computer's programs and devices. It acts as a waiting room where data sits until the device it needs to talk to is ready. This is really useful because different parts of your computer work at different speeds.
A common example of spooling is with printers. When you click 'print' on a document, the data doesn't go directly to the printer. Instead, it goes to a special area on your hard drive called a spool. Here, the document waits its turn until the printer is ready to handle it. This method is handy because it lets you continue using your computer for other tasks without waiting for each page to print.
How Does Spooling in Cyber Security Work?
In the context of cyber security, spooling ensures that information is managed in an organized way, reducing the chances of data problems or unauthorized access. Here's how it typically works:
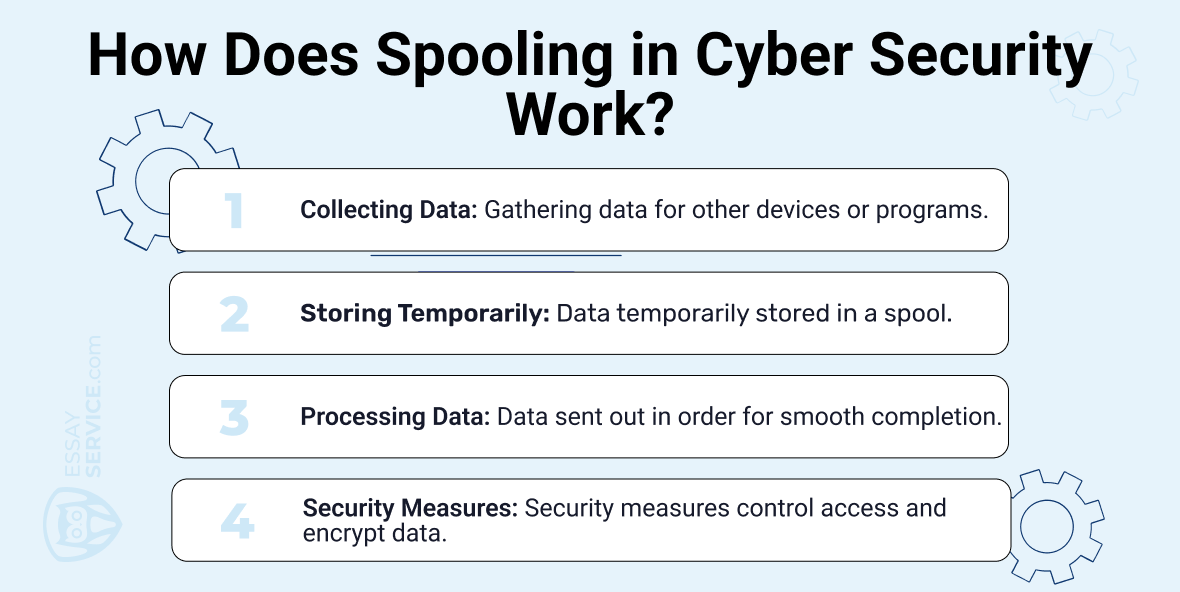
- Collecting Data: Spooling starts by gathering data meant for another device or program. This could be anything like a document waiting to print, an email to send, or files to process.
- Storing Temporarily: After gathering, the data sits in a temporary storage area called a spool, often on the hard drive. This spool keeps the data safe while waiting for its turn to be handled.
- Processing Data: When the right device or program is ready, the spool sends out the data in the order it was received. This step-by-step process helps avoid mix-ups and ensures each task gets done smoothly.
- Security Measures: To make things safer, different security measures are put in place. These can be things like controlling who can access the spool, keeping track of who's been using it, and making sure the data is encrypted to stop unauthorized access.
Swamped with Schoolwork?
Our expert writers will help you stay on top of your assignments, freeing up your time for other priorities!
Pros and Cons of Spooling in Cyber Security
Spooling in cyber security offers a mix of benefits and potential risks, making it essential to understand both sides to effectively manage and secure data. Let's explore these aspects:
Benefits of Spooling in Cyber Security
- Efficiency: Spooling makes systems work better by letting devices and programs operate without waiting for each other. This speeds up tasks and makes everything run more smoothly, boosting overall productivity.
- Resource Management: It helps manage system resources more effectively. By lining up tasks, systems can use memory and processing power better, avoiding overload and making sure each task gets enough attention.
- Error Handling: Spooling can cut down on mistakes in data processing. If a device or program isn't available for a bit, the data stays in the spool until things are fixed, instead of causing a breakdown or losing data.
- Prioritization: Some spooling systems can prioritize tasks. Important jobs can jump ahead in line, making sure vital processes happen first.
Potential Risks of Spooling in Cyber Security
- Data Vulnerability: While data sits in the spool, it could become a target for unauthorized access. If not properly secured, sensitive information may be at risk.
- Resource Exhaustion: If the spooling system isn't managed well, it can lead to resource exhaustion. Large volumes of data waiting to be processed might consume substantial system resources, leading to slowdowns or crashes.
- Complexity in Management: Managing spooling systems, particularly in a large or dynamic environment, can be complex. This complexity might lead to misconfigurations, which in turn can expose vulnerabilities.
- Dependency on Storage: Since spooling in cyber security relies on temporary storage, any issues with the storage system (like corruption or failure) can impact the entire spooling process, potentially leading to data loss or system downtime.

How to Protect Your System?
To leverage the benefits of spooling in cyber security while minimizing its risks, it's important to implement and manage it carefully. Here are some strategies for implementing it safely and tips for effective management:
4 Ways of Implementing Spooling Safely
- Make sure the folders where data is spooled have the right permissions to keep them safe.
- Keep sensitive information safe by encrypting files stored in the spool, as it stops unauthorized people from getting in.
- Check the spooling process regularly for anything strange to catch any security issues fast.
- Keep systems that use spooling up to date with the newest security fixes. Many cyber-attacks use holes that updates would fill in.
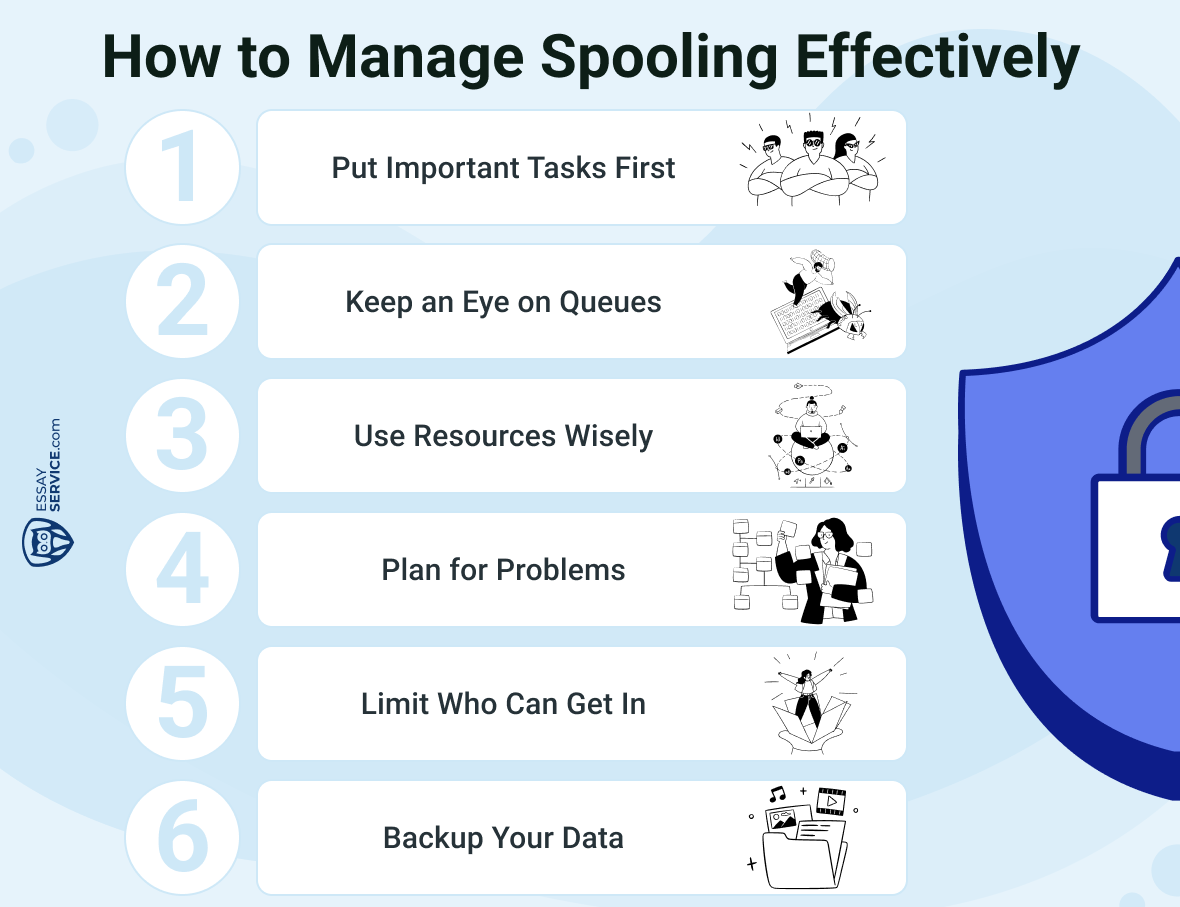
6 Tips for Managing Spooling Effectively
- Put Important Tasks First: Make sure critical tasks get done first by setting up a system that prioritizes them. This helps things run smoothly and quickly.
- Keep an Eye on Queues: Watch how big the spool queues get. Put limits in place to stop them from getting too big, which can slow things down and even crash the system.
- Use Resources Wisely: Make sure your system has enough disk space and memory to handle spooling tasks without slowing down.
- Plan for Problems: Set up backup plans in case something goes wrong with the spooling system. This helps minimize downtime and keeps your data safe.
- Limit Who Can Get In: Only let people who really need it use the spooling system. This cuts down on the risk of someone messing with important data.
- Backup Your Data: Regularly save copies of spooled data. This helps protect against losing data if something goes wrong with the system, like a crash or a security breach.
Feeling the Essay Crunch?
Our team of skilled academic writers is here to ease your burden and help you conquer your workload.
A Bottom Line
In wrapping up, spooling in cyber security organizes and manages data transactions systematically, reducing the risk of security breaches that might happen if data were handled carelessly. Following the safety measures and management tips ensures that spooling boosts both the security and efficiency of your IT system.
New posts to your inbox!
Your submission has been received!


.png)
.png)